Introduction
It’s been over a year since the most destructive and expensive ransomware attack on the healthcare industry, an incident that sent shockwaves to nearly every corner of the practice of medicine. The recovery, which persists to this day, has been painstaking and, indeed, embroiled in controversy. But are there still lessons that can be learned from this devastating breach? All signs point to yes, as it seems little to no progress has been made on a concerted effort to shore up the number one most targeted industry in the world.
In this article, we will explore the genesis of the Change Healthcare ransomware attack, analyze UnitedHealth Group’s initial response to the incident, reflect on the price tag that came along with the incident and its aftermath, and review five key lessons that every healthcare provider must learn from this situation, lest they become the next target of a band of not-so-merry misfits.
Breach Overview & Timeline
Picture it: the Cybersphere, February 2024. In the early morning hours of February 21, Optum (which acquired Change Healthcare in 2021) reported company-wide “connectivity issues” related to Change’s systems. Optum immediately disconnected their primary systems from Change’s to isolate the disruption. But let’s back up… Optum? UnitedHealth Group? Change Healthcare? Who exactly are all the players? Let’s start with a brief introduction.
Who Is Change Healthcare?
Change Healthcare is a subsidiary within a subsidiary within a gigantic corporate conglomerate. Let’s start at the top and work our way down.
UnitedHealth Group: One Group to Rule Them All
UnitedHealth Group (UHG) is the uppermost organization in the spiderweb of divisions it governs. UHG had revenues of over $370 billion in FY2023 and employed more than 400,000 people across all of their child companies. For those of you playing the home game, that’s roughly the population of Tampa, FL. UHG is the largest healthcare insurance company, but insurance is only a small part of what UHG has in their portfolio. UHG is broadly divided into two major divisions: United Healthcare (the insurance side) and Optum (the “everything else” side).
Optum
Optum is classified as a “healthcare services” company that offers everything from pharmacy services to care delivery to data analytics. Their mission statement is to “create a healthier world, with you at the center.” Their 2023 revenue exceeded $220 billion and they employ over 200,000 people worldwide. Their subsidiaries are three: OptumHealth (care delivery and management, including home and ambulatory care), OptumRx (the third largest Pharmacy Benefit Manager (PBM) by market share), and OptumInsight (data analytics, technology, and consulting services as well as revenue cycle and payment management systems).
Change Healthcare
Acquired in 2022 for $8 billion, Change Healthcare was a behemoth in the payment management space. As one of the largest financial and administrative information exchange operations, it moved billions of dollars per year through its revenue cycle management ecosystem and issued insurance payments to hospitals, providers, pharmacies, and more.
Attack Vector & Timeline
The attack was discovered in the early morning hours of February 21, 2024. Initially reported as “enterprise-wide network connectivity issues,” word quickly got out that the disruption was the result of a cyberattack. The disruption across the healthcare industry was almost immediate, as critical systems became encrypted by the ransomware deployed by the attackers.
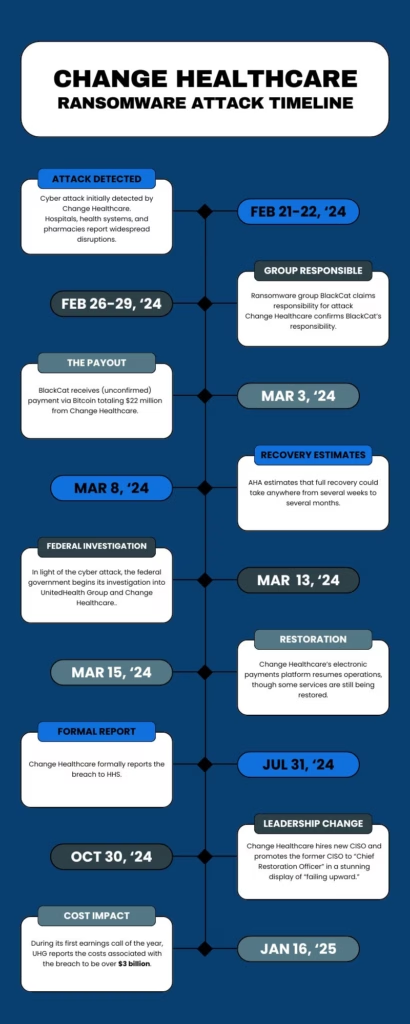
Over a year hence, we still don’t have specifics about the exact attack vector, though several theories have been presented. Several reports have indicated that it was a vulnerability in the “Remote Desktop Protocol” used by IT systems to access devices such as remote servers and other workstations; others attribute the initial ingress point to a Citrix vulnerability (Citrix is also a remote access tool used by companies to provide “virtual” desktops to their workforce). Whatever the initial ingress point, the attack proceeded with vigor, quickly encrypting critical resources and bringing Change Healthcare to its technological knees.
Immediate Impact
The full scale of the disruption became painfully evident in a matter of hours. Critical systems across thousands of healthcare providers, ranging from small family practices to large hospital networks, suddenly froze, unable to process claims, submit pre-authorizations, or verify patient eligibility. Pharmacies were similarly hit, losing their ability to confirm medication coverage, creating immediate bottlenecks in dispensing essential medications.
Diagnostic imaging providers found themselves in a digital limbo; patient scans, reports, and images could neither be uploaded nor accessed. Even worse, providers faced an alarming silence from Change Healthcare and Optum in those first critical hours. Without clear guidance or updates, confusion spread rapidly, compounding the disruption. The domino effect meant thousands of patient appointments and procedures had to be delayed or canceled outright, significantly impacting patient care.
Financial implications were equally severe. With claims processing halted, revenue streams for healthcare organizations quickly dried up. Many providers, particularly smaller ones operating on thin margins, found themselves in immediate cash flow crises, illustrating just how delicate (and dependent) our healthcare payment ecosystem has become on third-party clearinghouses.
Root Cause & Contributing Factors
Vendor Risk Management Gaps
Change Healthcare’s ransomware event exposed glaring blind spots in vendor risk management across the healthcare industry. Organizations relying on Change Healthcare had limited visibility into the security posture of Change’s internal systems. Few providers had enforceable audit rights or meaningful oversight, leaving them blind to vulnerabilities hidden deep within their vendors’ networks.
Insufficient Incident Response Coordination
When chaos struck, communication broke down rapidly. Healthcare providers dependent on Change Healthcare struggled to find accurate, real-time information about the breach. The absence of clearly established communication protocols meant precious hours were wasted attempting to confirm the status and severity of the outage, exacerbating delays in activating their internal incident response plans.
Over-Reliance on Third-Party Infrastructure
The attack painfully highlighted how extensively healthcare providers depend on single vendors for critical operations. Without alternative processing pathways or backup vendors, many providers had no practical failover options. This over-dependence turned what might have been a localized disruption into an industry-wide crisis.
Technical Vulnerabilities
Investigations later revealed the usual suspects behind such breaches: missed patches, weak backup protocols, inadequate endpoint monitoring, and insufficient lateral movement controls. These seemingly small technical oversights opened the door wide for the ransomware actors and allowed the malware to proliferate across Change Healthcare’s expansive infrastructure.
Five Key Lessons Learned
1. Don’t Underestimate Your BAs
The attack on Change Healthcare demonstrated that even major vendors can represent a significant cybersecurity risk. Providers must treat every business associate, regardless of size or reputation, as a potential entry point for cyber threats. Conduct rigorous, regular vendor assessments, insist on independent security audits, and enforce audit rights through clear contractual language.
2. Network Segmentation Is Critical
Proper network segmentation could have significantly mitigated the spread of ransomware within Change Healthcare’s infrastructure. Micro-segmentation, which restricts internal network communication to only what’s explicitly necessary, can drastically reduce attackers’ lateral movement. Providers must implement strict segmentation policies, especially around critical infrastructure and vendor-connected systems.
3. Test Your Incident Response Playbook
Many providers discovered the hard way that their incident response plans hadn’t adequately accounted for third-party outages. Regular tabletop exercises and practical drills simulating vendor disruptions are essential. These exercises should explicitly test the effectiveness of vendor-down communication plans and failover strategies.
4. Ensure Data Redundancy & Failover Paths
The heavy reliance on Change Healthcare underscored the necessity of redundancy and failover capabilities. Providers must have backup vendors or alternative processing pathways ready to activate immediately should a primary vendor become compromised. Continuity planning is not optional; it’s an operational imperative.
5. Communicate Quickly & Transparently
Delayed or unclear communication during the breach magnified downstream confusion and frustration. Providers must have pre-approved communication templates and clearly defined escalation paths ready to deploy rapidly in the event of a breach. Transparency and clarity reduce panic, streamline response efforts, and maintain stakeholder trust.
Applying These Lessons Today
Implementing automated vulnerability scanning tools can quickly identify potential “fat-finger” or inadvertent vendor access vulnerabilities. Continuous scanning ensures that providers proactively address these risks before they are exploited.
Regularly embedding business associate-specific cybersecurity questions into compliance questionnaires helps maintain heightened vigilance. Centralizing and controlling versions of vendor management policies ensures consistency and enforceability across all partnerships.
Continuous monitoring of third-party endpoints, cloud integrations, and data exchanges provides real-time insights into vendor-related threats. This proactive stance allows immediate remediation when anomalies are detected.
Establish a centralized vendor risk dashboard that captures real-time vendor security postures, historical incident data, and compliance status. Such visibility allows informed, data-driven decisions regarding vendor relationships and risk mitigation.
Checklist: Post-Breach Readiness
Would you know what to do if your systems were compromised today? Discovering the attack is the very beginning of a series of crucial and time-sensitive steps that must be taken in order to mitigate the spread of the attack (be it ransomware, malware, or a virus). Below are some immediate next steps to take if you discover that your systems have been compromised:
- Isolate Affected Systems Immediately: Disconnect compromised servers and endpoints from the network to contain the spread.
- Activate Your Incident Response Team: Notify internal incident response leads immediately and initiate your response protocols.
- Preserve Evidence: Document exactly what occurred and preserve logs and snapshots for forensic investigation.
- Notify Critical Stakeholders: Alert senior leadership, legal counsel, and cybersecurity insurance providers immediately.
- Engage External Experts: Contact cybersecurity forensic specialists if needed, especially if internal resources are limited.
- Begin Breach Notification Protocols: Follow your communication plan to inform affected business associates, providers, and patients as required by law.
- Report to Law Enforcement and Regulatory Authorities: Notify the FBI, CISA, or appropriate authorities promptly, as per regulatory requirements.
- Assess Backup Integrity and Begin Restoration: Determine the status of backup systems and initiate restoration procedures using verified clean backups.
- Provide Clear and Regular Updates: Establish frequent communication updates to all impacted parties, including internal teams, partners, and regulators.
- Document Everything: Maintain a meticulous, detailed log of all actions taken, communications sent, and steps completed during response efforts for compliance and legal protection.
Conclusion & Call to Action
The Change Healthcare ransomware incident painfully underscored the vulnerabilities inherent in our interconnected healthcare infrastructure. Providers must proactively embrace the lessons learned from this breach, fortifying their cybersecurity defenses and ensuring robust contingency measures are firmly in place.
Healthcare organizations, both large and small, cannot afford complacency. Consider scheduling a demo of MediGuard360 Sentinel today to evaluate and enhance your vendor risk management and incident response capabilities. After all, in cybersecurity, prevention is always cheaper and far less stressful than recovery.
